Deploying IDP for OCP
In this lab we will deploy a IDP connection to your OCP cluster to provide Authentication and Authorization.
We will use the AutoAD Active Directory VM as the IDP as it is already installed in your HPOC/SPOC cluster.
Setup IDP
This setup can also be done using the OCP Cluster Manger GUI. But in this section we will use commands.
Depending on you access to
kubeconfigfile or kubeadmin password, logon to the OCP cluster- kubeconfig
- kubeadmin
- NCM
Export your kubeconfig file to envexport KUBECONFIG=/root/xyz/auth/kubeconfigMake sure to use your passwordoc login -u kubeadmin -p xxxxx-xxxxx-xxxxx-xxxxxIn Calm go to your Applications > Openshift xyz1 application
Go to the Services
Select your LB_DNS service
Click on Open Terminal
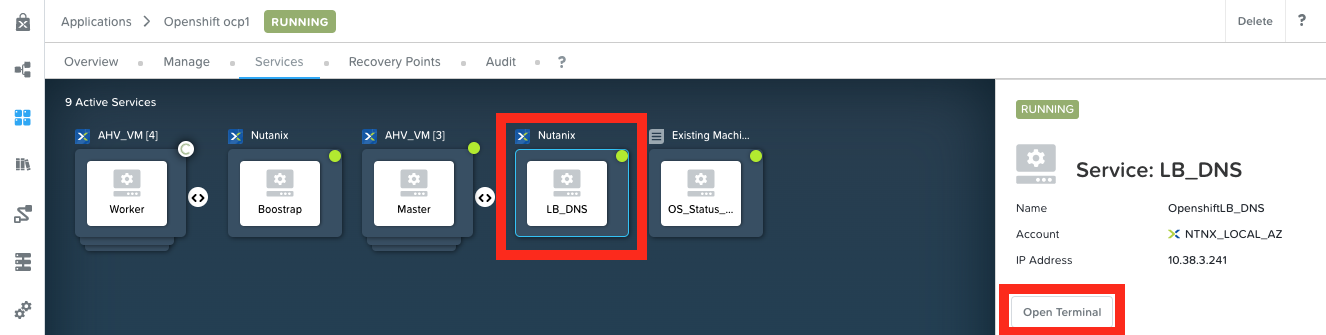
The terminal will open in a new browser tab
export KUBECONFIG=~/openshift/auth/kubeconfig
Execute the following commands in sequence
# Create a kubernetes secret for AutoAD administrator password
oc create secret generic ldap-secret --from-literal=bindPassword='nutanix/4u' -n openshift-configSetup the OAuth provider
cat << EOF | oc apply -f -
apiVersion: config.openshift.io/v1
kind: OAuth
metadata:
name: cluster
spec:
identityProviders:
- name: ntnxlab.local
mappingMethod: claim
type: LDAP
ldap:
attributes:
id:
- sAMAccountName
email: []
name:
- displayName
preferredUsername:
- sAMAccountName
bindDN: administrator@ntnxlab.local
bindPassword:
name: ldap-secret
insecure: true
url: ldap://dc.ntnxlab.local/CN=Users,DC=ntnxlab,DC=local?sAMAccountName
EOFCreate the LDAP sync config file
echo """kind: LDAPSyncConfig
apiVersion: v1
url: ldap://dc.ntnxlab.local:389
bindDN: administrator@ntnxlab.local
bindPassword: "nutanix/4u"
insecure: true
groupUIDNameMapping:
CN=SSP Admins,CN=Users,DC=ntnxlab,DC=local: OCP_SSP_Admins
CN=SSP Operators,CN=Users,DC=ntnxlab,DC=local: OCP_Cluster_Operators
augmentedActiveDirectory:
groupsQuery:
baseDN: CN=users,DC=ntnxlab,DC=local
scope: sub
derefAliases: never
pageSize: 0
groupUIDAttribute: dn
groupNameAttributes: [ cn ]
usersQuery:
baseDN: cn=users,dc=ntnxlab,dc=local
scope: sub
derefAliases: never
filter: (objectclass=person)
pageSize: 0
userNameAttributes: [ sAMAccountName ]
groupMembershipAttributes: [ memberOf ]""" > ldapsync.yamlSetup the LDAP sync
oc adm groups sync --sync-config=ldapsync.yaml --confirmCreate rolebinding using the following commands
oc adm policy add-cluster-role-to-group cluster-admin OCP_SSP_Admins
oc adm policy add-cluster-role-to-group console-operator OCP_Cluster_Operators
If you logout of the OCP cluster manager Web UI. You will be able to see two authentication mechanisms(instead of just 1 before):
- Local - kubeadmin
- ntnxlab - ntnxlab.local

Verifying Authentication and Authorisation
Now that we have setup connectivity for OCP to Active Directory as ID provider, we can now check which user (authentication) is allowed to perform what action (authorization).
Cluster Admin
- In the OCP Web UI login page, select ntnxlab.local
- Enter the following credentials
- Username - adminuser01
- Password - nutanix/4u
- Observe what management capabilites are available for adminuser01
- Take a screenshot of the login page and add it to you validation screenshot bundle
Cluster Operator
- In the OCP Web UI login page, select ntnxlab.local
- Enter the following credentials
- Username - operator01
- Password - nutanix/4u
- Observe what management capabilites are available for operator01
You have sucessfully configured authentication and authorisation for OCP with Active Directory as IDP.
Challenge
Assign the following groups to be able to access OCP.
| AD User Group | OCP Role |
|---|---|
| SSP Admins | cluster-admin |
| SSP Operators | cluster-operator |
You will need to modify the config file in step 7 (ldapsync.yaml) to include these. Identify the format of specifying this and add on configuration per line.
You will have run the following command in step 9 to add a admin policy
oc adm policy add-cluster-role-to-group <cluster role> <group name>
You have successfully completed integrating Active Directory with OCP Cluster for Authentication and Authorisation.